You can integrate your Active Directory Federation Services (ADFS) instance to help manage seamless single sign-on for your members. Keep reading to learn more! 👇
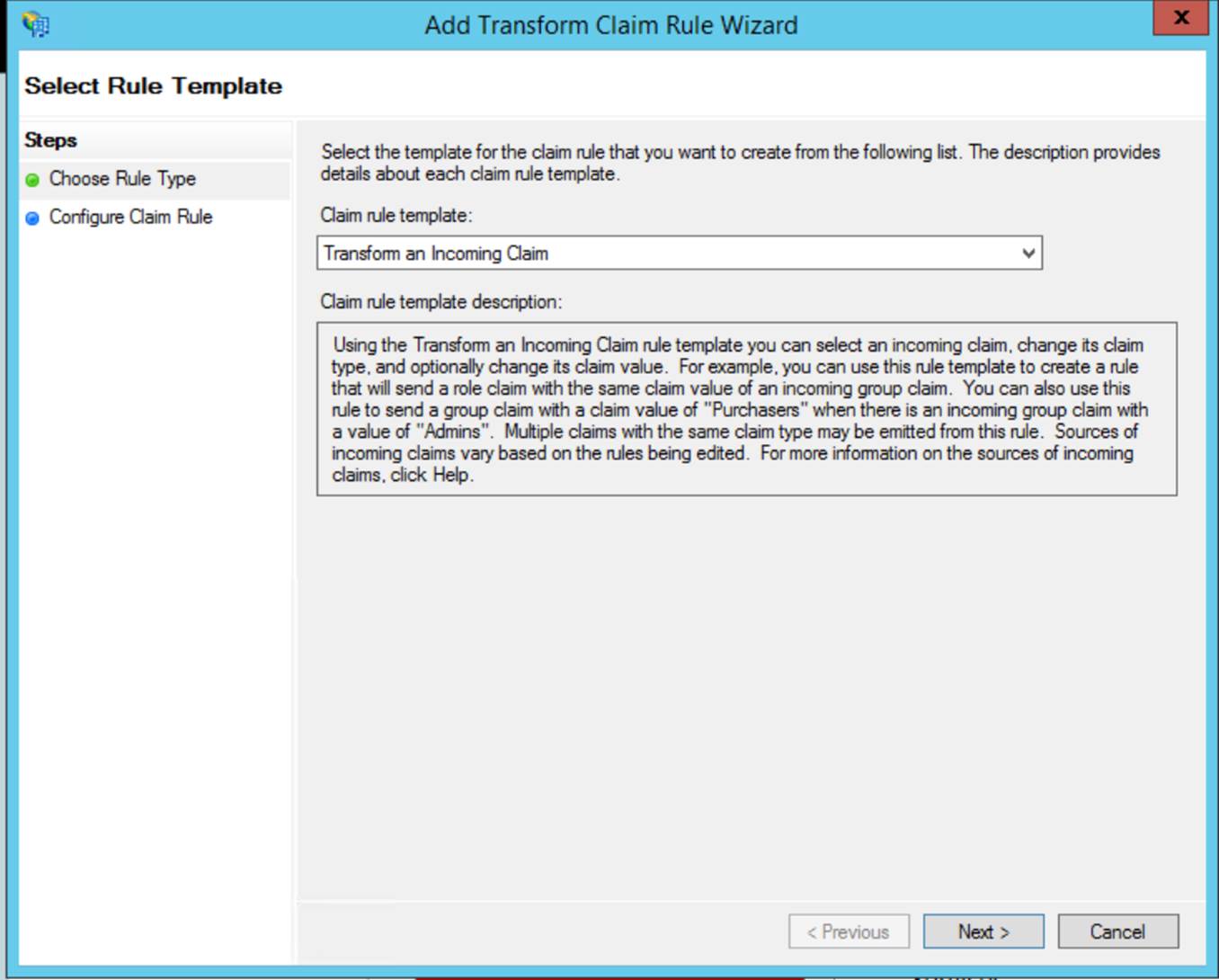
Step 1
Configure the relying party using the metadata file that can be found here:
https://<YOUR_DOMAIN>.monday.com/saml/saml_metadata
Step 2
Next, you'll create rules, or assertion claims, for your relying party trust — in this case, your monday.com account.
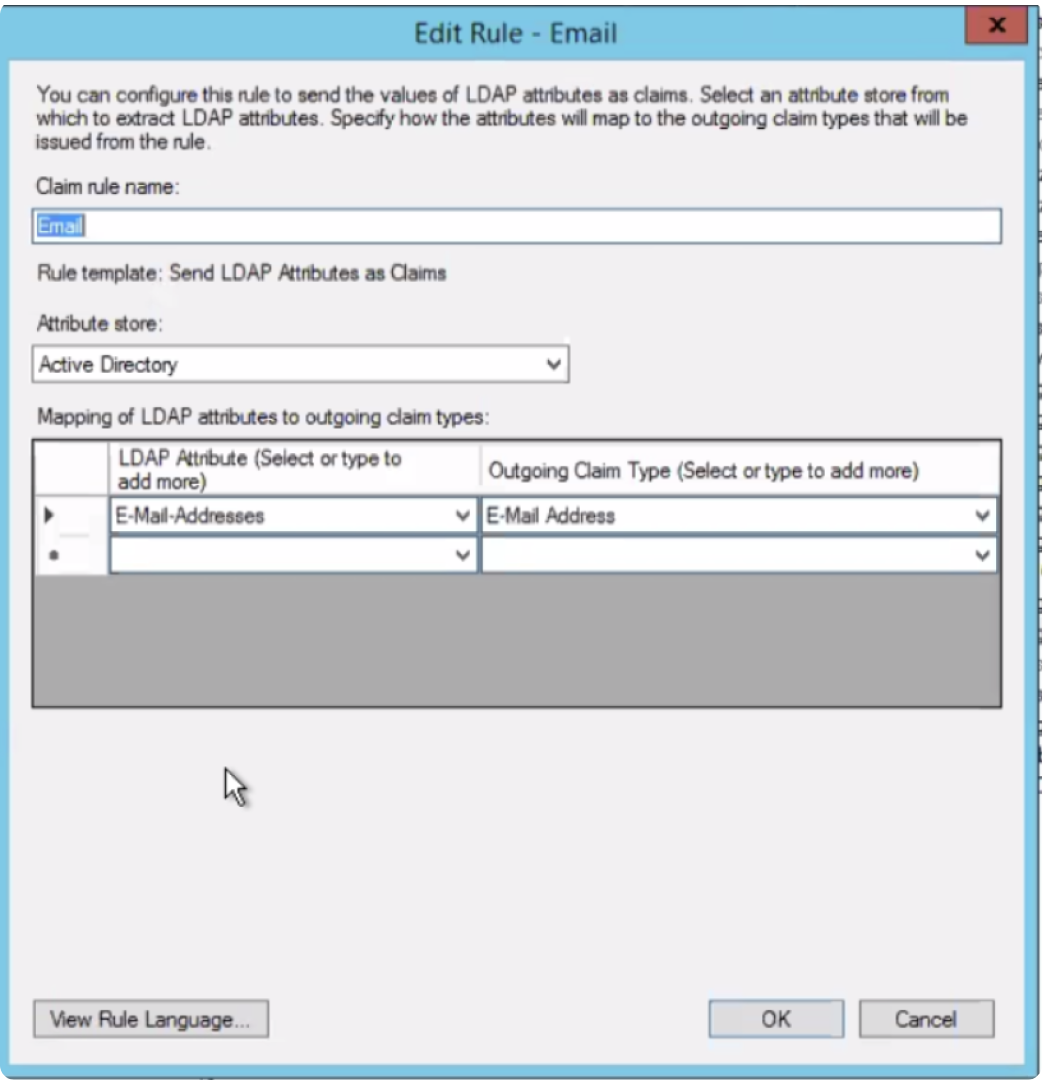
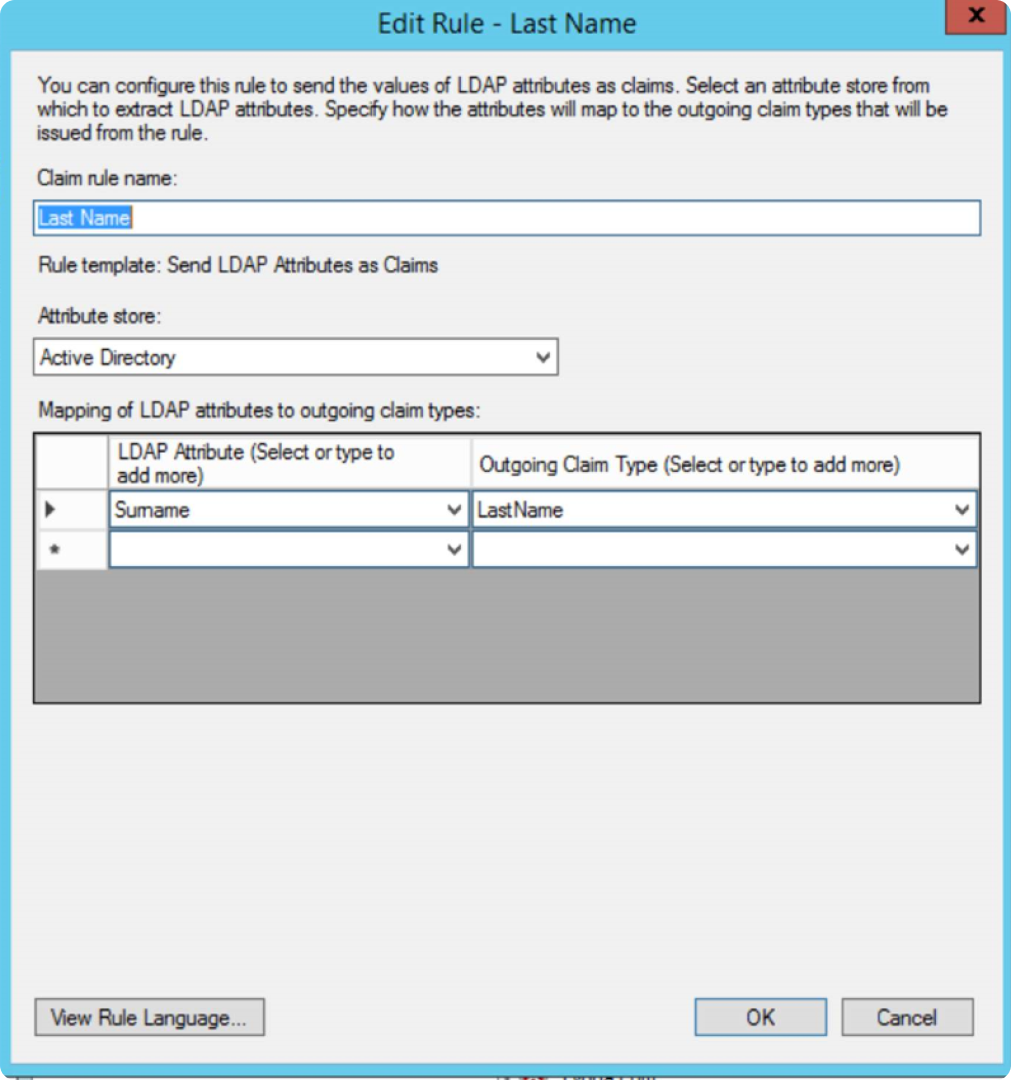
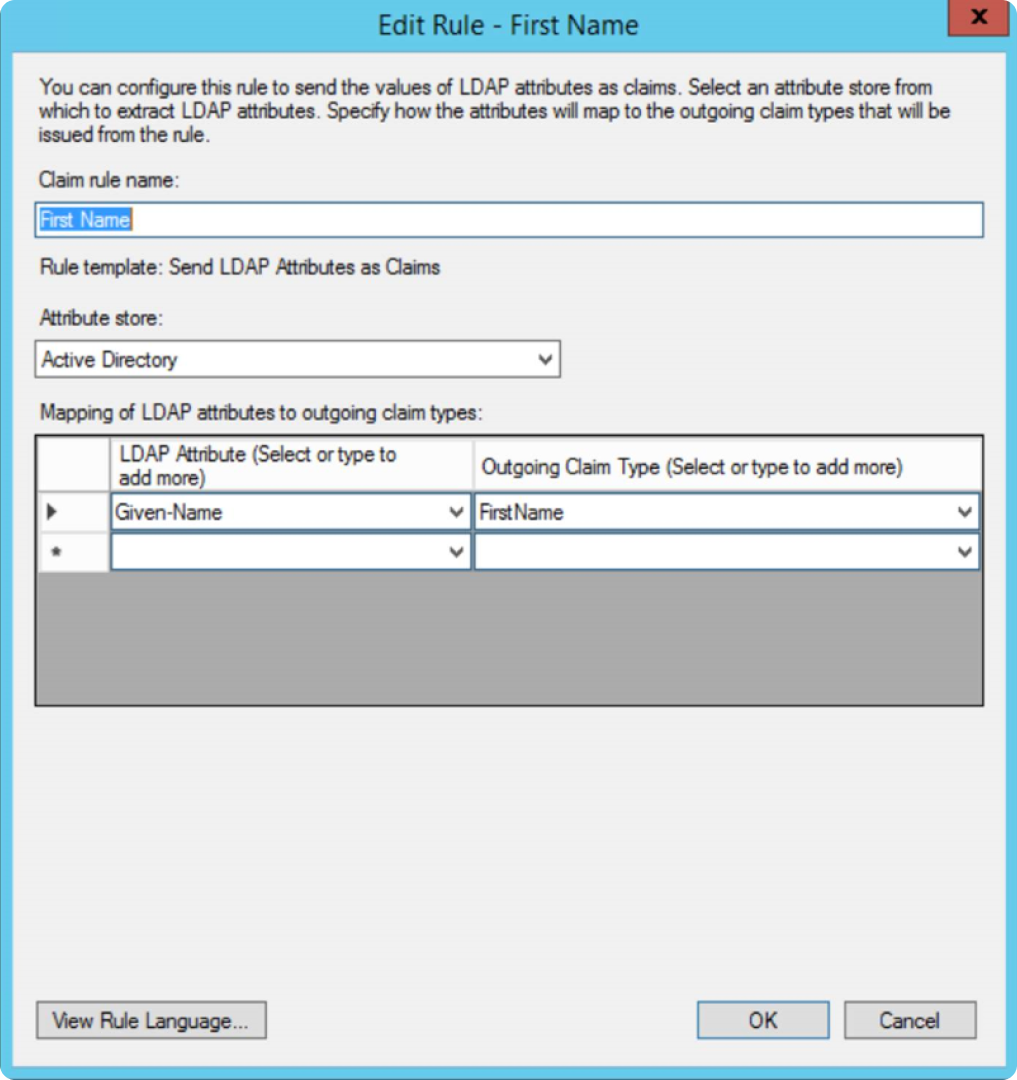
monday.com only receives the outgoing claim type attributes and values, so the list of attributes might look different. Keep in mind, you will need two claims: one for monday.com Attributes and one for NameID. To create a new rule, click on "add rule". For example, the first one we will create is "Email".
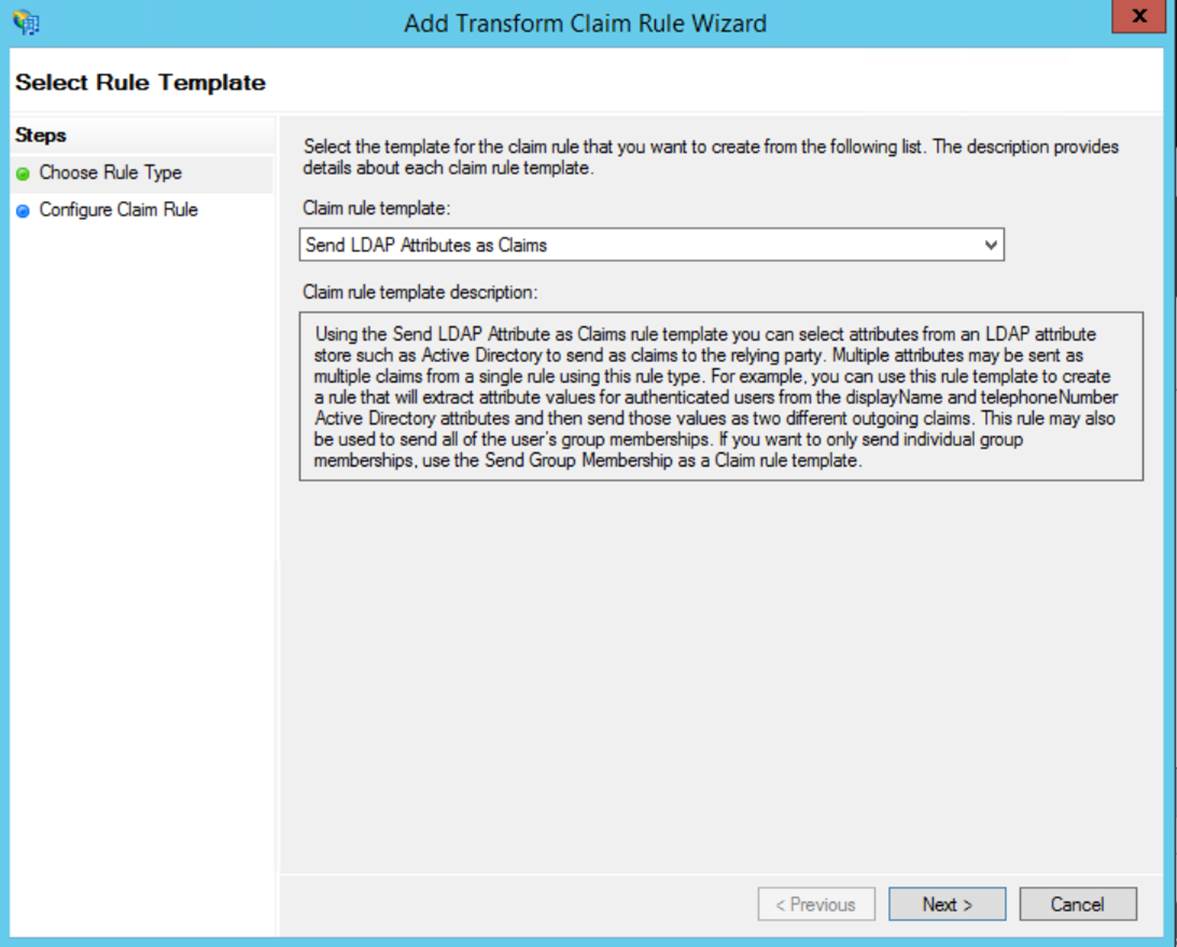
Step 3
Create a rule to send LDAP attributes as claims. Remember, outgoing claim types are case sensitive. The claims supported by monday.com are: Email, FirstName, LastName.
Step 4
You can now edit the rule as below:
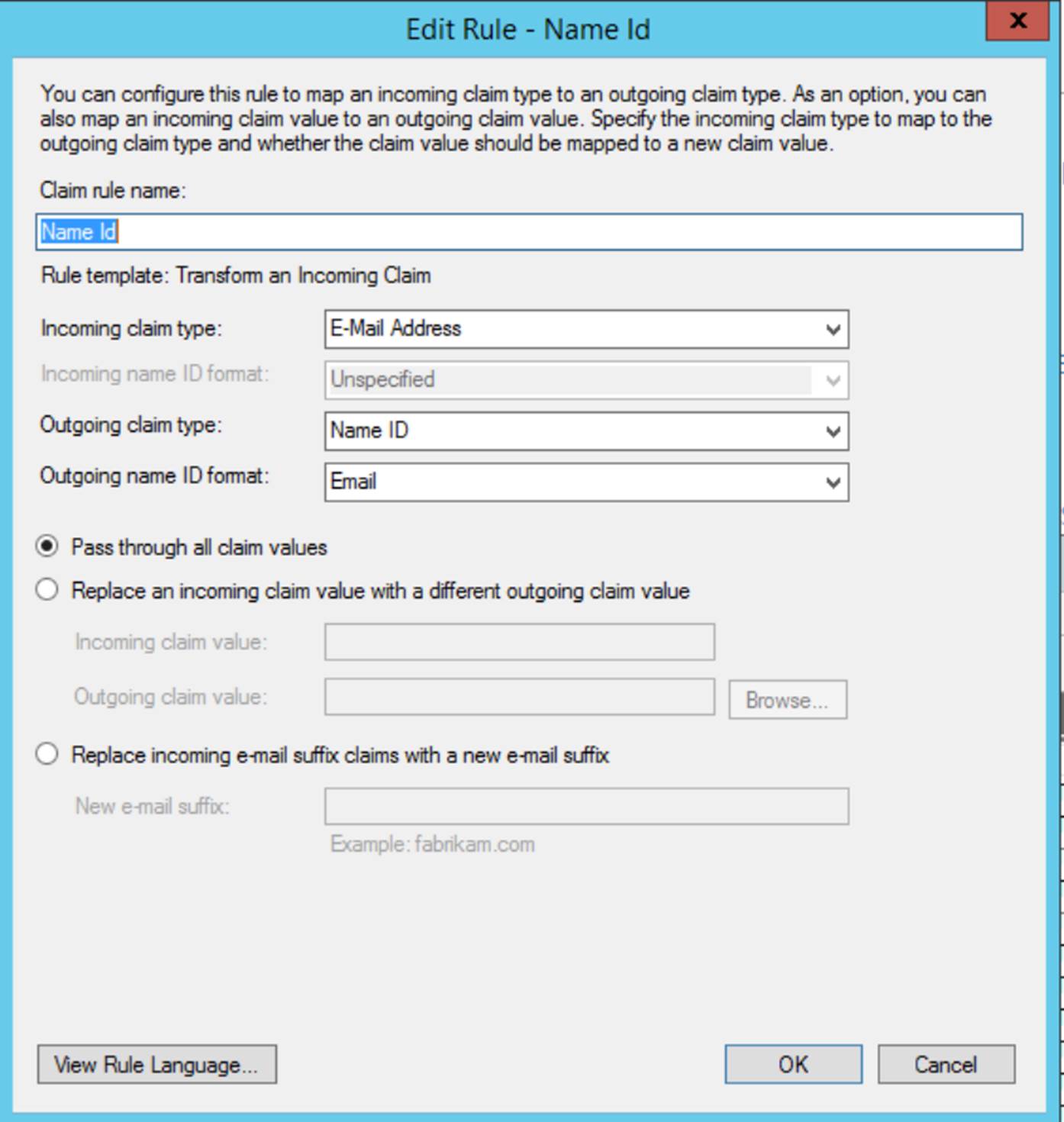
Step 5
Next, create another rule to transform an incoming claim.
Integrate monday.com with your IDP
https://support.monday.com/hc/en-us/articles/360000460605-SAML-Single-Sign-on
If you have any questions, please reach out to our team right here. We’re available 24/7 and happy to help.
Comments